PDF) Protocols for Authentication and Key Establishment Second Edition | Ernesto Dominguez Fiallo - Academia.edu
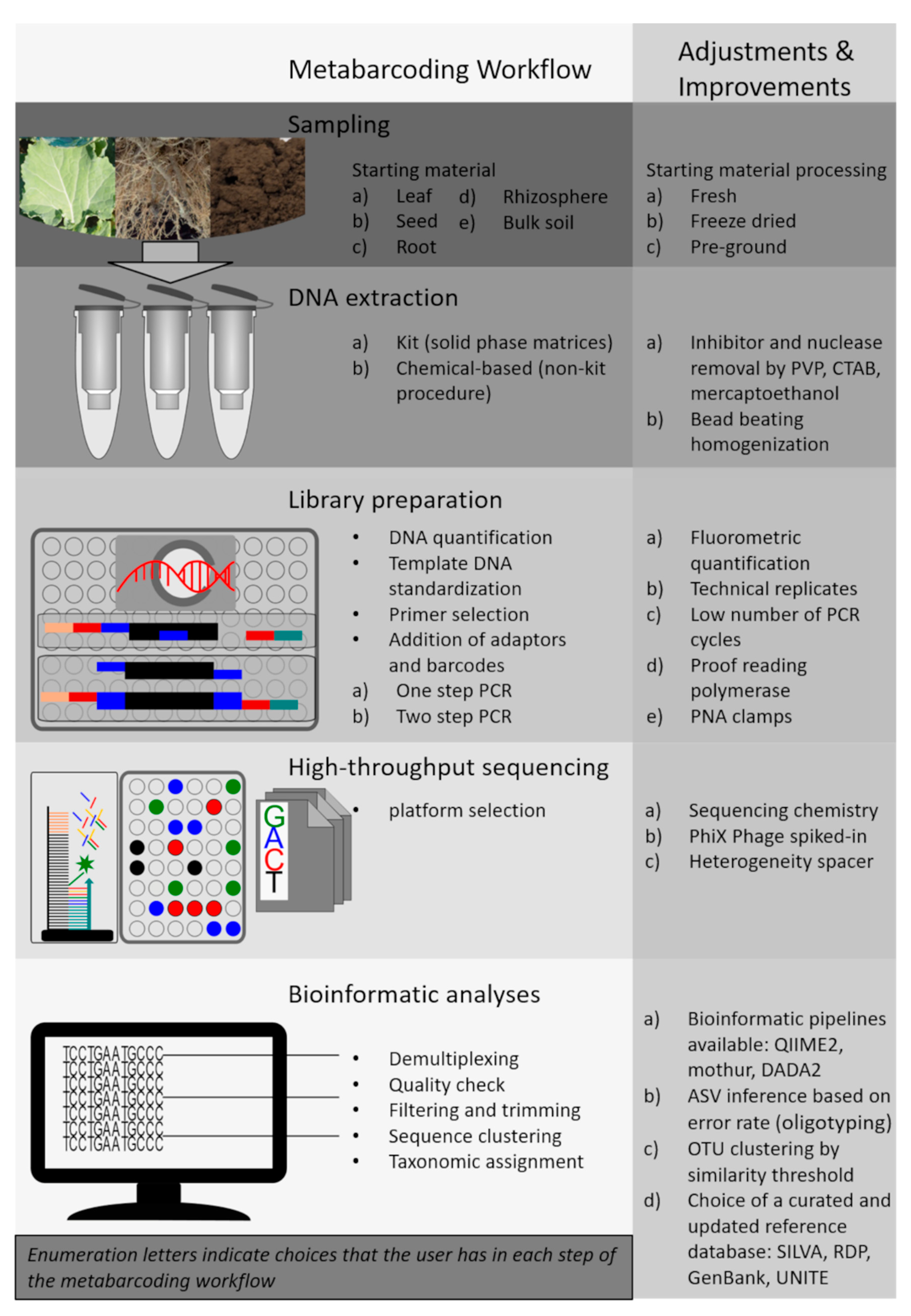
Microorganisms | Free Full-Text | DNA Metabarcoding for the Characterization of Terrestrial Microbiota—Pitfalls and Solutions
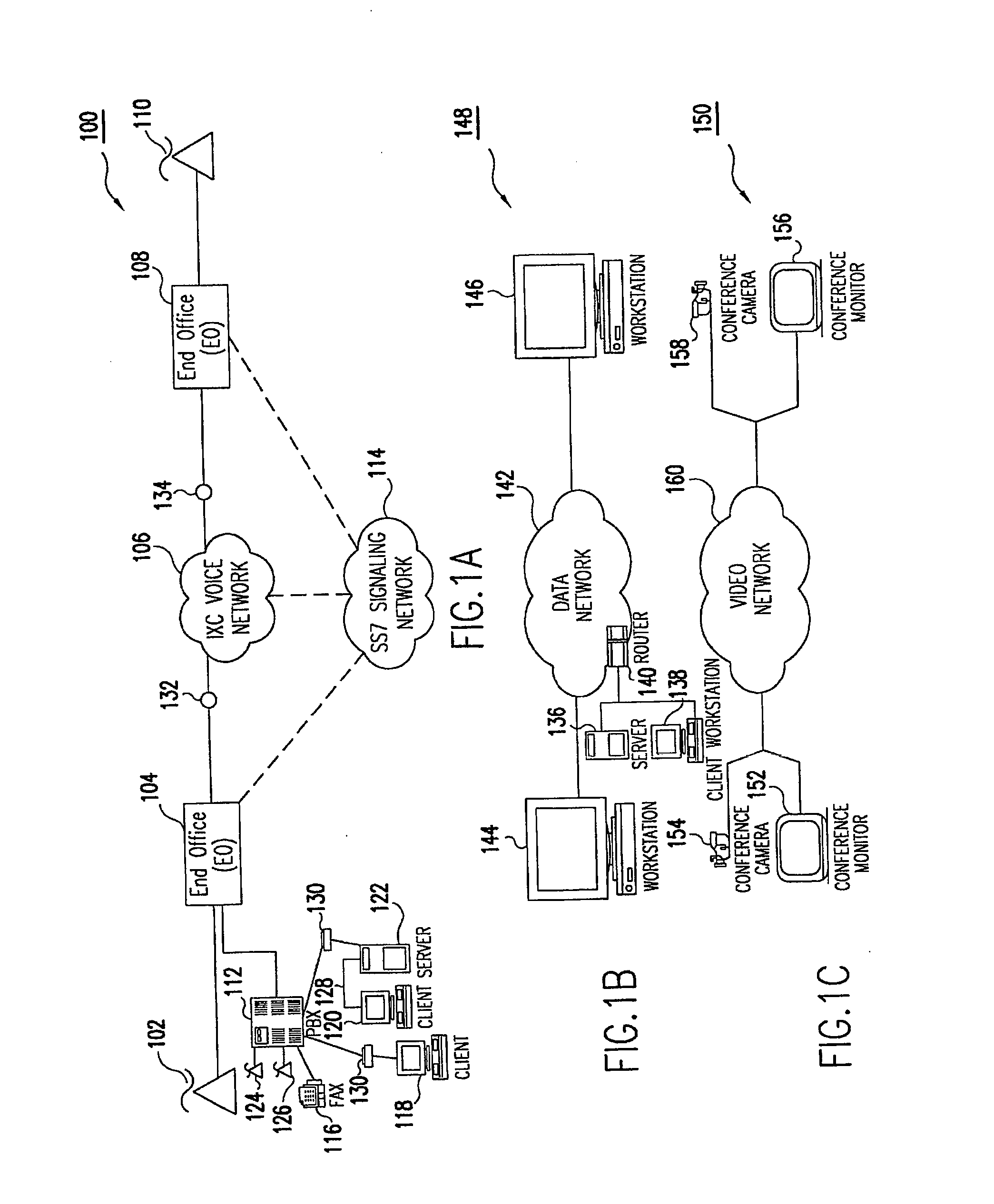
TRANSMISSION CONTROL PROTOCOL/INTERNET PROTOCOL (TCP/IP) PACKET-CENTRIC WIRELESS POINT TO MULTI-POINT (PtMP) TRANSMISSION SYSTEM ARCHITECTURE. Патент № US 20120257527 МПК H04W24/00 | Биржа патентов - Московский инновационный кластер
![An improved primer set and amplification protocol with increased specificity and sensitivity targeting the Symbiodinium ITS2 region [PeerJ] An improved primer set and amplification protocol with increased specificity and sensitivity targeting the Symbiodinium ITS2 region [PeerJ]](https://dfzljdn9uc3pi.cloudfront.net/2018/4816/1/fig-1-2x.jpg)
An improved primer set and amplification protocol with increased specificity and sensitivity targeting the Symbiodinium ITS2 region [PeerJ]

Computer Security and PGP: What Is Diffie - Hellman Key Exchange Protocol or Oakley Protocol? | Computer security, Security, Secret
![Systems and methods for large scale OTA firmware update Patent Grant Oakley , et al. April 12, 2 [Shure Acquisition Holdings, Inc.] Systems and methods for large scale OTA firmware update Patent Grant Oakley , et al. April 12, 2 [Shure Acquisition Holdings, Inc.]](https://uspto.report/patent/grant/11303516/US11303516-20220412-D00000.png)
Systems and methods for large scale OTA firmware update Patent Grant Oakley , et al. April 12, 2 [Shure Acquisition Holdings, Inc.]

Amazon.com: OhO Bluetooth Sunglasses,Voice Control and Open Ear Style Smart Glasses Listen Music and Calls with Volume UP and Down,Bluetooth 5.0 Audio Glasses and IP44 Waterproof : Electronics